
In today’s rapidly evolving technology landscape, “Software as a Service” (SAAS) has emerged as a game-changer, transforming the way businesses and individuals access, use, and manage software applications. Learning SaaS, whether you’re a seasoned IT professional or a curious newcomer, offers a plethora of advantages that can enhance your career prospects and personal growth. In this blog post, we’ll explore five compelling advantages of learning SaaS and why it’s a skill worth acquiring.
Accessibility and Convenience
One of the most significant advantages of SaaS is its accessibility and convenience. Unlike traditional software that requires installation and maintenance on individual devices, SaaS applications are hosted in the cloud. This means you can access them from anywhere with an internet connection and on any device. Learning how to use SaaS applications effectively empowers you to work, collaborate, and stay productive while on the go, whether you’re at home, in the office, or on vacation.
Cost-Efficiency
SaaS offers a cost-effective alternative to traditional software licensing. With SaaS, you typically pay a subscription fee, which covers software updates, maintenance, and customer support. This eliminates the need for costly upfront investments in software licenses, hardware, and IT infrastructure. By mastering SaaS tools, you can help your organization reduce its software-related expenses and allocate resources more efficiently.
ALSO READ: Pros and Cons of Using Windows Hosting in 2023
Scalability
The scalability of SaaS is another significant advantage. Whether you’re a small business looking to grow or a large corporation with fluctuating software needs, SaaS applications can easily adapt to your requirements. You can increase or decrease the number of user licenses, storage capacity, or other resources as your needs change. Learning SaaS allows you to harness the full potential of this scalability, ensuring your software resources align with your business demands.
Automatic Updates and Maintenance
SaaS applications are known for their seamless and automatic updates. With traditional software, you often have to manually download and install updates, which can be time-consuming and sometimes disruptive. SaaS providers handle updates and maintenance in the background, ensuring that you always have access to the latest features, improvements, and security patches. Learning how to manage SaaS applications helps you stay current with technology and safeguards your data and systems.
Collaboration and Integration
Collaboration is at the core of many SaaS applications. Learning how to use tools like Google Workspace, Microsoft 365, or Slack can significantly enhance your ability to work with colleagues and clients. SaaS applications also tend to integrate with other software, offering a seamless ecosystem for your workflow. By mastering SaaS, you can streamline your work processes, share documents more efficiently, and facilitate better communication with your team.
Conclusion
Learning SaaS is not just a skill; it’s an investment in your future. Its accessibility, cost-efficiency, scalability, automatic updates, and collaborative features make it a valuable asset for both individuals and businesses. As the technology landscape continues to evolve, proficiency in SaaS applications becomes increasingly essential for staying competitive and efficient. So, whether you’re an entrepreneur looking to streamline your operations or an IT professional aiming to expand your skill set, diving into the world of SaaS is a smart move. Embrace the advantages of SaaS, and you’ll find yourself well-equipped for the challenges of the modern digital age.
ALSO READ: Why Should You Invest in Laravel Development?

In the ever-evolving landscape of web hosting, making the right choice for your website’s hosting platform is crucial. With the variety of options available, it’s essential to weigh the pros and cons of each before making an informed decision. One such option is Windows Hosting, a choice that has been in the market for several years and has evolved over time. In this blog post, we’ll delve into the pros and cons of using Windows Hosting in 2023, to help you determine if it’s the right fit for your web hosting needs.
Understanding Windows Hosting:
Before we dive into the advantages and disadvantages, let’s briefly understand what Windows Hosting entails. Windows Hosting is a web hosting solution that employs Microsoft’s Windows Server operating system to manage and deliver website content. It’s a popular choice for websites that are built using technologies such as ASP.NET, .NET Core, or those that require integration with Microsoft tools like Microsoft SQL Server or SharePoint.
Pros of Using Windows Hosting in 2023:
- Compatibility with Microsoft Technologies: One of the standout benefits of Windows Hosting is its seamless integration with Microsoft technologies. If your website relies heavily on ASP.NET, .NET Core, or other Microsoft frameworks, Windows Hosting provides an optimized environment for these technologies to run smoothly.
- Support for Microsoft Databases: Windows Hosting offers excellent compatibility with Microsoft databases, including Microsoft SQL Server. If your website requires a robust and scalable database solution, Windows Hosting can efficiently manage your database needs.
- User-Friendly Interface: Windows Hosting typically includes the Plesk control panel, which offers a user-friendly interface for managing various aspects of your hosting environment. This is particularly advantageous if you’re not well-versed in server management.
- Security Features: Windows Server comes with advanced security features that can help protect your website from various online threats. Regular updates and patches from Microsoft contribute to a secure hosting environment.
- Remote Desktop Access: Windows Hosting allows for remote desktop access, which can be handy for certain administrative tasks and configurations. This feature can be beneficial if you need direct control over your server environment.
Cons of Using Windows Hosting in 2023:
- Cost: Windows Hosting tends to be more expensive than alternative hosting solutions, such as Linux Hosting. Licensing fees for Windows Server and associated Microsoft software can contribute to higher hosting costs.
- Resource Intensive: Windows Hosting can be more resource-intensive compared to Linux Hosting, which might lead to slightly slower performance on lower-tier hosting plans. This might not be ideal for websites with high traffic or resource demands.
- Limited Open Source Compatibility: While Windows Hosting has made strides in supporting open-source technologies, it may still have limitations when it comes to hosting websites built on popular open-source platforms like WordPress or Joomla.
- Dependency on Windows Updates: While regular updates are essential for security, Windows updates can sometimes lead to compatibility issues with certain applications or scripts running on your website.
- Less Common for Certain Web Applications: Windows Hosting is not always the best choice for certain types of web applications or scripts. Many developers and webmasters prefer Linux Hosting for applications like PHP, Perl, or Python-based websites.
Conclusion:
As you evaluate your web hosting options in 2023, it’s essential to consider the specific requirements of your website and the technologies it relies on. Windows Hosting can be an excellent choice if your website is built using Microsoft technologies and if you require seamless integration with Microsoft databases. The user-friendly interface and security features also make it a compelling option for businesses and individuals who value convenience and data protection.
However, the higher cost, potential resource intensity, and limited open-source compatibility should also be taken into account. If your website relies heavily on open-source technologies or if you’re working within a budget, Linux Hosting might be a more suitable option.
In the end, the decision between Windows Hosting and other hosting solutions depends on your unique needs and priorities. By carefully weighing the pros and cons outlined in this blog post, you’ll be better equipped to make an informed choice that aligns with your website’s goals and requirements in 2023 and beyond.
ALSO READ: 5 Best and Popular CMS Platforms of 2023

AngularJS and ReactJS are two of the most popular JavaScript frameworks for building web applications. Both are widely used by developers across the globe, and both have their own strengths and weaknesses. In this blog post, we will explore the differences between AngularJS and ReactJS and try to determine which one is best for 2023.
First, let’s take a look at AngularJS. AngularJS is a comprehensive framework for building complex, single-page web applications. It was first released in 2010 by Google and has since become one of the most popular frameworks for web development. AngularJS uses a declarative programming style and is based on the Model-View-Controller (MVC) architecture. It also comes with a range of features and tools that make it easier to build scalable and maintainable applications.
ReactJS, on the other hand, is a library for building user interfaces. It was developed by Facebook and was first released in 2013. Unlike AngularJS, ReactJS is focused on the View layer of an application and does not provide a complete MVC framework. Instead, ReactJS uses a component-based architecture, which makes it easier to build reusable UI components.
So, which one is better for 2023? Well, it really depends on your specific needs and requirements. AngularJS is a great choice if you need a complete framework for building complex web applications. It comes with a range of features, such as data binding, dependency injection, and testing tools, that make it easier to develop and maintain large-scale applications. AngularJS also has a large and active community, which means that there are plenty of resources and support available for developers.
On the other hand, ReactJS is a great choice if you are looking for a lightweight library for building user interfaces. Its component-based architecture makes it easier to build and reuse UI components, which can save you time and effort in the long run. ReactJS is also highly performant and can handle large amounts of data and complex UI interactions with ease. Additionally, ReactJS has a growing and active community, which means that there are plenty of resources and support available for developers.
Another factor to consider when choosing between AngularJS and ReactJS is your team’s skills and experience. If your team is already familiar with AngularJS, it may be easier and faster to continue using it rather than switching to a new framework like ReactJS. Similarly, if your team has experience with ReactJS, it may make more sense to stick with it rather than learning a new framework like AngularJS.
In terms of popularity, both AngularJS and ReactJS have a strong following and are widely used by developers. According to the State of JS 2020 survey, ReactJS is the most popular front-end framework/library, with 71% of respondents saying they have used it before. AngularJS came in third place, with 39% of respondents saying they have used it before. However, it’s worth noting that the survey also showed that ReactJS usage is growing faster than AngularJS usage.
Ultimately, the choice between AngularJS and ReactJS comes down to your specific needs and requirements. Both frameworks have their own strengths and weaknesses, and both can be used to build high-quality web applications. If you need a comprehensive framework for building complex web applications, AngularJS may be the better choice. If you are looking for a lightweight library for building user interfaces, ReactJS may be the better choice. Whichever framework you choose, make sure to take the time to learn it thoroughly and leverage the resources and support available from the community.
ALSO READ: Shopify or Magento Which One to Choose For Your eCommerce Development

Has your computer become too slow and is acting a bit odd? Are you losing your sleep over fixing the issue but can’t really figure out what’s wrong? If this is your scenario then the computer might have got virus.
Once a computer detects virus, it starts showing signs like slow performance, frequent pop-ups, or even data lose. But how do you identify a computer virus and defend yourself? Well, that’s what we’ll discuss in this article.
What Is A Computer Virus?
A computer virus is a type of program that successfully modifies other applications with its code. If the execution process is done right, the modified areas of that application are known as infected areas. They often damage the software and steal your personal information stored in that software. Generally, more than thousands of computers get affected by viruses and malware every year.
How To Detect A Virus In Your Computer?
The following signs will help you identify a virus in your computer.
Performance Level Drops
As we mentioned earlier, a virus can easily hamper your computer’s performance levels drastically. For instance, your machine can take 2 hours to copy a 50MB file.
Spams And Pop-Ups
Spams and pop-ups are some of the prominent red flags. Whenever you visit a dicey website, pop-ups can easily install harmful malware. Hackers use spam and pop-ups to hijack personal information like credit card details, passwords, and many more.
Unable To Gain Access To Some Files
In some cases, a virus can prevent you from accessing some files on your own computer. It can also stop you from performing certain actions like log off, power off, and more.
Security Software Failure
Often, when a computer gets affected by a virus, your security software or antivirus program stops running. It is a primary sign to confirm your computer has a virus or malware.
Changes In Your Homepage
Sometimes, a virus can easily change all the settings on your homepage. For example, your homepage browser is changed, shortcut files, browsing errors, and more.
How to Defend Your Computer From Virus Attacks?
The following points will help you defend your computer from virus attacks.
Perform Security And Virus Scans In Regular Interval
To prevent virus attacks, perform security and virus scans at regular intervals. This will routine clean all the malware and virus from your computer.
Changes Passwords
Use strong passwords that meet requirements like symbols, alphabets, numbers, uppercase, and lowercase letters. Also, try changing them in regular intervals to prevent yourself from getting hacked.
Use Good Antivirus Software
Using antivirus software is probably one of the best ways you can prevent virus attacks. They always monitor your computer and will notify you instantly about any suspicious activity.
Download From Trusted Sites Only
Always download from reputable and trusted websites. Thus, the chances of getting a virus with your downloaded files gets thin.
Use Pop-Up Blocker Extension
A pop-up blocker is a great way to block unwanted ads. We recommend you to avoid clicking on pop-ups. So, the chances of malware and virus attacks also decrease.
Update Antivirus
This is perhaps the most important part of keeping your antivirus relevant. If you don’t update, the software won’t handle all new viruses in the market.
Conclusion
Virus attacks are real, and they can easily damage files, hack your personal information, and crash your operating system. So, while preparing to save your computer from virus attacks, this article will surely help you out.

In the past few decades, information technology has become an integral part of our daily lifestyle. In fact, many people will say that it has taken over people’s lives. Just take a moment and look around you. You will see a world filled with gadgets, computers, and other tech stuff. Smartphones are perhaps the most important belonging for most people nowadays.
However, with all these dependencies, information technology has its own set of pros and cons when it comes to its impact on modern society. In this article, let us discuss the impact of information technology on modern society and its future.
The Impact Of Information Technology On Modern Society:-
The following points will showcase some of the positive and negative impacts information technology has on today’s society.
Positive Impact of Information Technology
Effective Communication
With the rise of Information technology, communication has become more simple and effective. For example, you can effectively communicate with anyone through emails, social networks, video calls, and more. From business deals to live interactions, technology has made it all easy.
Fast And Interactive Learning
Technological advancement also helps us to practice interactive and fast learning. It gives us access to all the available resources in the digital world, and that too 24*7. For example, students can easily prepare themselves for exams, sitting in their bedrooms. Moreover, teachers can also help them through online classes and video calls.
Easy Availability
One of the best things about technological advancements is that almost everything is easily available. Of course, this has its own drawbacks. But the truth is that you can get anything you want from the internet, for example, groceries, electronics, information, books, and more.
Negative Impact of Information Technology
Reduced Physical Activity
With all these technological advancements, you can easily expect some downsides. For example, the rise of technology is making people lazier than ever. Nowadays, kids prefer mobile games and play stations over playing outside on an open field.
Data and Privacy Protection
Perhaps the biggest concern of technological advancement is the lack of data and privacy protection. Advanced machine learning has given birth to sophisticated drones and robots. They can easily monitor our daily activities. Moreover, your data on your smartphone is not entirely secured.
The Future Of Information Technology
However, with all these good and bad sides, information technology has a foreseeable future. The following points will shed a light on the possible future of information technology.
Energy-Efficient Vehicles
The concept of electric cars is very much a reality. But in upcoming years, we will possibly witness a world where all vehicles will be eco-friendly to reduce carbon footprints.
Virtual Reality
The game called Pokémon Go has given this world a sneak-peek into virtual reality. But with Facebook announcing the Meta Verse, virtual reality definitely has a bright future.
Education For All
The number of people who cannot afford education around the world is staggering. But with internet access, we will possibly witness a world where the literacy rate will reach its peak.
Conclusion:-
Information technology has definitely cast a strong impact on modern society. And this impact will increase in the foreseeable future. However, it all depends on us and how we use it to make this world a better place.
Also Read:- Impact of mobile apps in our future life
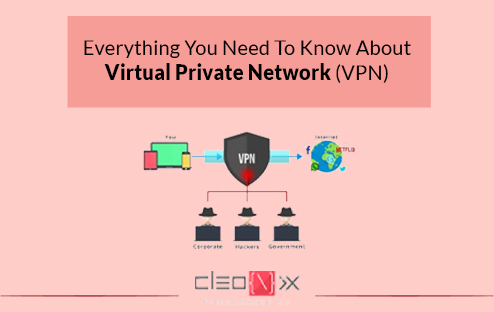
If you are an active user of the internet or even fairly frequent on the internet, one term must have come across many a times- VPN. But most people go on about their regular internet usages without putting much thought into what a “VPN” is, like several other tech-savvy jargon they hear and ignore on a daily basis. Let’s change that and take a look at what is a VPN and what is it all about.
A Virtual Private Network or VPN for short, is meant for the particular purpose of securely extending a network from one private location and enabling its users to connect to other networks securely. What are the most common utilities that come with a VPN? Let’s take a look at few instances that are actually quite common and relatable nowadays. We know about the often imposed internet censorship in different regions in the world where authorities restrict the access to certain contents or/and websites. Or that “rumour” that the government is always tracking everyone’s browsing activity or the fact that there is actually a threat to privacy invasion from random people looking to exploit. Well, a VPN can help you in all these instances and more. It’s no surprise the VPN market is on the way to grow bigger and bigger.
Read also: Advantages of using LESS
So, let’s have a look at some more benefits that a Virtual Private Network offers:-
- Maintaining privacy and anonymity from ISPs- Internet service providers are pretty keen on tracking their subscribed customers to try and monetize on the browsing patterns by various means such as targeted advertisement, etc. These providers also tend to sell this data to third-parties who can further misuse this information. Using a VPN, such invasion of privacy can be avoided.
- Accessing shopping websites from different regions- The VPN can allows you to access shopping websites, which are otherwise inaccessible due to region-based restrictions.
- Staying protected in public wi-fi- We all often tend to connect to the free wi-fi at public places like hotels, restaurants, shopping malls, railway stations, etc. But in doing so, we are actually getting connected to an unsafe network where we are exposed and so is our private data and credentials. A VPN comes handy at such times by masking our identity, making us anonymous and keeping our personal data private and unexposed.
- Prevention from hackers- As we discussed already, VPN masks the IP address and hence the identity of an individual connected to a certain network. Hence, any hacker trying to target your network via your IP address will be thrown off as they simply can’t reach your home network.
Read also: Use of blockquote in HTML
To sum it up, a VPN has a lot of pros as it provides us with a secure encrypted network, disguises our location data, helps in accessing region-restricted content and also secure data transfer to prevent any confidential data leaks. Although there are numerous VPN services available today, but like every other technology, some are good, some bad and some ugly. So, one should do their fair share of research and use the right VPN for enjoying all the benefits of a VPN without compromising with the security.

As we all see nowadays, everything around us has gone digital. Web-centric is the new way to be for everyone including more or less all established businesses. Be it small, medium or a large enterprise, businesses have adapted to stay relevant and to maintain their presence in the market, they need to have an online presence and a well maintained one at that. But being an online business is a much complex endeavor than it sounds.
An online business is one that can sell its products or services to its customers via the internet. Ensuring a smooth flow of business via the means of internet is a complex task- being present and being noticed are not enough. All online businesses are competing against each other to be more useful, attractive and interesting so as to hold the attention of their potential customers or clients.
A website that can’t offer the state-of-the-art features, simply starts losing out on potential customers and hence, revenue. The ease of access as well as a good user experience are of utmost importance. To provide a completely optimum UX for the target audience, an online business needs to take care of many factors in their website and/or app. One such major factor is the feature of online payments.
Online payments are made possible by the means of web payment gateway and is an almost indispensable feature for most e-commerce websites. All online businesses want to offer the freedom of paying online to their customers for an easy transaction. In fact, the success of any e-commerce business nowadays relies on the ease and number of facilities the customers are getting while purchasing from the said business- be it via their credit card, debit card or net banking.
Read also:- 5 reasons why having a website is necessary for every business
A web payment gateway is a tool which provides an online payment processing system, where a customer shares their details in a secure way, following which the details are verified and the funds are transferred from the customer to the merchant. Utilizing payment gateways are simply smart and convenient for all. The system is empowered with encryption technology to help securely verify the data or information a customer provides so as to minimize the instances of fraudulent activities.
Let’s take a look at the key benefits of using web payment gateways by an online business:
• As all transactions happen through a proper organized channel, the fund-flow of sales and similar transactions is very well managed.
• All communication regarding the transactions are with responsible entities like bank, processor and other associated bodies which makes it so easy and hassle free.
• All kinds of transfer done between the point of payment and point of sale are over a secure network, which prevents unnecessary glitches or risks.
• Payment gateways play such an important role in the secure transfer, interpretation and direction of data while also preventing any losses or delays.
So, in conclusion, every online business needs to have a good web payment gateway system working for them and helping them to grow in this tech-savvy world.
Read Also:- SMS Marketing- Uses & Benefits To Strengthen Your Business

Over the years, security concerns have gone up regarding any data and digital attacks have rather become commonplace. Hackers and piracy are everywhere targeting valuable information, posing a serious threat to the businesses. Now, we have seen that in recent times, videos and live video-streaming have seen such a boom that every modern business uses this digital tool for connecting to their consumers. There are several varieties of live-streaming that act as a great opportunity and marketing tool to reach a large audience base. So how can this process be made secure and safe from unwarranted attacks!! Although there are actually several protocols and methods developers try to follow to protect your videos with a secure live streaming solution, let’s take a look at the best seven ways to do so:
- Advanced Encryption Standard Encryption->
Advanced Encryption Standard or AES encryption method is used to encode the information that can be only viewed by authorized users. In this encryption method, a special key is used, without which the video can’t be viewed. This is a very simple and easily implemented process.
- HTTPS Delivery->
Whenever a user uses an open network at a public place, they are prone to certain attacks by hackers looking to steal data that is being transmitted to such users. HTTPS Delivery utilizes HLS encryption to prevent such attacks by using digital certificated and encryption keys.
- Password-Protection of Videos->
As simple as the name suggests, this method simply uses a password being set for the video. A user needs to have the correct password in order to be able to watch said video content. It is an effective method despite its simplistic nature. Keep changing the password from time to time and stay ahead of any leaks or risks.
- Secure video paywall via SSL/TLS->
A secure video paywall that uses SSL/TLS encryption can protect the user’s payment information from being stolen while also allowing you to monetize the video streaming and accept multiple currencies and cards.
- IP Restrictions->
IP restrictions or geographical restrictions are a good option for content that is meant to be targeting audience from selected regions by allowing you to block certain “risk-zones” that usually generate most of the data-theft attempts.
- Referrer Restrictions->
Referrer restrictions are pretty useful as they allow only selected domains to stream the videos and restricts playback on any other unauthorized website.
- Content Delivery Network->
Content Delivery Network or commonly known as the CDN is a network of servers that runs secure video data centers to store the video files online. A live-streaming CDN enables the video content to load faster. Online video platforms that use a CDN are very effective against several kinds of attacks and also offer protection from hardware-failure.
The main thing to understand to ensure secure live streaming is that we must employ various techniques that work best depending on our type of content, variety of target audience as well as kind of expected threats. Regular monitoring is a must so that we can stay one step ahead of the potential threats. All data and information is precious and should be protected by all means necessary.

What is Webp?
WebP is an open-source image format designed to work with web browsers. The goal is to create smaller images that will speed up the internet. Speed up the creation of web pages and you can speed up search engines. Google is introducing this photo format in 2010. The format allows users to either save an image in a lossless or lossless format. Google made bold claims about the format’s compression capacity that it could be up to 34 percent lower than the JPEG or PNG file equivalent. Google assumes that the speed of the internet as a whole can be improved by implementing a more effective image format due to the volume of images displayed at any time around the world. WebP loss compression operates by a forecasting technique. That pixel block is estimated on the basis of other pixel blocks surrounding it. The difference is then encoded between prediction and truth. Because of the prediction technique’s performance, many of the blocks contain a zero difference resulting in higher compression and therefore a smaller file size. WebP lossless compression works by using already analyzed parts of the image to create other parts of the image.
You may like: Why does Microsoft really want you to stop using Internet Explorer?
Pros of WebP:
It is designed to use a compression algorithm that is more efficient and better balanced than JPG and PNG with the goal of minimizing file sizes with minimal loss of quality. And that means websites that use less bandwidth faster. This makes the users of your page happy, and it also makes Google happier — they now clearly prefer fast websites in their search rankings over slow ones.
WebP has two main attractions. One is the reduced file size without any apparent decline in quality. How much smaller WebP files are than their JPG counterparts varies by a number of factors, but the statistics of Google range from 25 to 35 percent larger. Google says that a 10 percent increase in page speed resulted from moving Youtube thumbnails to WebP.
The other main attraction is that the format incorporates features that were not traditionally incorporated in one format: incorporating the distinctive strengths of JPG, PNG, and GIF formats.
You may have seen WebP photos without knowing it. For a while, Facebook used it on its Android apps. You can find thumbnails in WebP if you open them in Chrome, Firefox or on an Android device. And while at the moment there is only a relatively small percentage of websites that use it, they are still out there.
What are WebP support browsers?
Chrome, Chrome for Mac, Firefox, Opera Mini and Android Browsers currently support WebP. Many major browsers may use the WebPJS JavaScript library to support the WebP format except for Flash-based Microsoft Explorer. You can also gain support for viewing and editing WebP formats on your local machine. For example, Google released a plugin that enables WebP images to work properly with Windows Photo Viewer and other components of Windows Imaging. Image editing software such as Photoshop can purchase a WebP format plugin.

Google is one of the many companies that offer free tools and services, such as Gmail, Google Analytics, and Google Docs. G Suite, Google’s smart app suite. This used to be known as Google Apps until it was re-branded at the end of 2016. This is where the GSuite Enterprise Edition for Google comes in handy.
G Suite will help you manage your company more efficiently, improve your workflow and improve your employee interaction. We will cover some of Gsuite’s benefits in this post to help you learn more about it.
1.Savings in the cost:
G Suite provides a collection of well-known applications like Gmail, Docs, Drive, and Calendar. The suite comes with apps that allow you and your team to work simultaneously on the same documents.
There is also an interactive chat platform that can be used to communicate and share ideas with you and your team. You can get all these apps for free, but with the paid service, you get more features. The efficacy has already been acknowledged by more than 3 million businesses.
G Suite can not beat for large-scale workplace organization for businesses on a budget. Moreover, conversion from an office server to G Suite eliminates expensive work orders and interruptions.
You may like: 5 Modern Web Forms Protection Solutions from Spam
2.Efficient coordination between teams:
The collection of smart applications from G Suite allows you and your team members to work together seamlessly on papers. You can see the edits you’re making in real-time and G Suite saves them in the cloud automatically.
You may offer all members of the team or just a selected few editing capabilities. When the employees are working on the papers, the built-in chat feature can be used. The technique of teamwork thus helps to develop a project’s speed and accuracy.
3.Data Security:
With Google Drive, you can safely store, access and share your files from any drive. To keep your data safe, G suite for business stores information in Google Data Centers. Besides, if the servers fail, you won’t lose your data, and all the information will remain in the cloud.
Besides, from G Suite, you have access to the devices of your employees. While G Business Suite provides the best level of security, it should be avoided via public Wi-Fi.
4.Google Vault:
Vault allows you to keep track of G suite items for corporate data like Gmail, Google Drive, Team and Group Chat and Hangouts. As it is the business part of G Suite, it is included in the pricing plans of the G Suite.
5.Easier Organization:
You can easily arrange meetings, plan tasks, record deadlines, and schedule appointments with the help of Google Calendar. Google Calendar is a centralized calendar that can be viewed, edited and shared by the entire company to set deadlines, meetings and project milestones. Through features such as color-coding to indicate changes and activity notifications sent directly to email, everyone can easily stay on track. The calendar is integrated with Gmail, allowing you to schedule events right in the inbox.
Through apps such as color-coding to indicate changes and activity notifications sent directly to email, everyone can easily stay on track. Gmail’s unified calendar helps you to arrange events right in the inbox.
GSuite offers some of the best tools for teamwork, management, and security, whether you’re a new business or a big business. Take the time to analyze your business needs and decide which edition best suits your business. In the comment section below, let’s share your thoughts with us!
About the author
Cleonix Technologies
A professional Web Development Company is highly focused on providing world class and best in the industry standard services in every domain that we work upon.

 AJ 14, Salt Lake, Sector 2, Kolkata - 700091 |
AJ 14, Salt Lake, Sector 2, Kolkata - 700091 |  743 Virginia Ave NE Atlanta, GA 30306
743 Virginia Ave NE Atlanta, GA 30306










